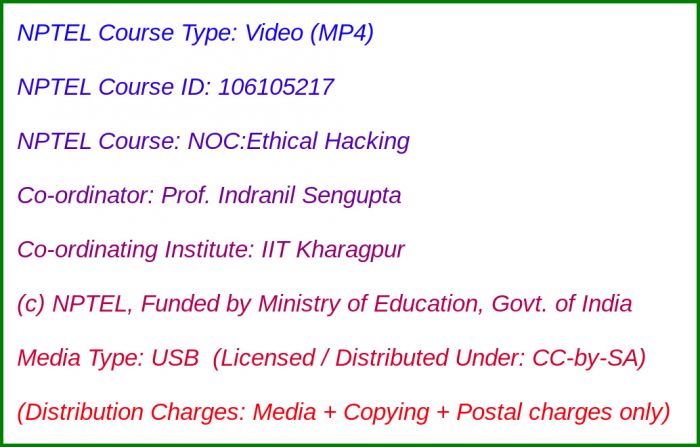
Media Storage Type : 32 GB USB Stick
NPTEL Subject Matter Expert : Prof. Indranil Sengupta
NPTEL Co-ordinating Institute : IIT Kharagpur
NPTEL Lecture Count : 62
NPTEL Course Size : 12 GB
NPTEL PDF Text Transcription : Available and Included
NPTEL Subtitle Transcription : Available and Included (SRT)
Lecture Titles:
Lecture 1 - Introduction to Ethical Hacking
Lecture 2 - Basic Concepts of Networking - Part I
Lecture 3 - Basic Concepts of Networking - Part II
Lecture 4 - TCP/IP Protocol Stack - Part I
Lecture 5 - TCP/IP Protocol Stack - Part II
Lecture 6 - IP addressing and routing - Part I
Lecture 7 - IP addressing and routing - Part II
Lecture 8 - TCP and UDP - Part I
Lecture 9 - TCP and UDP - Part II
Lecture 10 - IP subnetting
Lecture 11 - Routing protocols - Part I
Lecture 12 - Routing protocols - Part II
Lecture 13 - Routing protocols - Part III
Lecture 14 - IP version 6
Lecture 15 - Routing examples
Lecture 16 - Demonstration - Part I
Lecture 17 - Demonstration - Part II
Lecture 18 - Demonstration - Part III
Lecture 19 - Nessus Installation
Lecture 20 - How to use nessus
Lecture 21 - Metasploit Exploiting System Software - I
Lecture 22 - Metasploit Exploiting System Software - II
Lecture 23 - Metasploit Exploiting System Software and Privilege
Lecture 24 - Metasploit Social Eng Attack
Lecture 25 - MITM (Man in The middle) Attack
Lecture 26 - Basic concepts of cryptography
Lecture 27 - Private-key cryptography - Part I
Lecture 28 - Private-key cryptography - Part II
Lecture 29 - Public-key cryptography - Part I
Lecture 30 - Public-key cryptography - Part II
Lecture 31 - Cryptographic hash functions - Part I
Lecture 32 - Cryptographic hash functions - Part II
Lecture 33 - Digital signature and certificate
Lecture 34 - Applications - Part I
Lecture 35 - Applications - Part II
Lecture 36 - Steganography
Lecture 37 - Biometrics
Lecture 38 - Network Based Attacks - Part I
Lecture 39 - Network Based Attacks - Part II
Lecture 40 - DNS and Email Security
Lecture 41 - Password cracking
Lecture 42 - Phishing attack
Lecture 43 - Maloeware
Lecture 44 - Wifi hacking
Lecture 45 - Dos and DDos attack
Lecture 46 - Elements of Hardware Security
Lecture 47 - Side Channel Attacks - Part I
Lecture 48 - Side Channel Attacks - Part II
Lecture 49 - Physical Unclonable Function
Lecture 50 - Hardware Trojan
Lecture 51 - Web Application Vulnerability Scanning
Lecture 52 - SQL Injection Authentication Bypass - Part 1
Lecture 53 - SQL Injection Error Based - Part 2
Lecture 54 - SQL Injection Error Based from Web Application - Part 3
Lecture 55 - SQLMAP
Lecture 56 - Cross Site Scripting
Lecture 57 - File Upload Vulnerability
Lecture 58 - The NMAP Tool: A Relook - Part I
Lecture 59 - The NMAP Tool: A Relook - Part II
Lecture 60 - The NMAP Tool: A Relook - Part III
Lecture 61 - Network Analysis using Wireshark
Lecture 62 - Summarization of the Course